- Solutions
- Digital Forensics & Incident Response (DFIR)
Data mining done in hours.
Canopy's AI & robust toolbox help you find PII, PHI, and high-risk data faster than any other software on the market.
Explore Canopy's AI-Powered PII Detection
Download our brochure to learn more.
See Canopy In Action
Canopy's Data Breach Response software leverages machine learning at every step, from PII detection through to generating a notification list.
As a digital forensics and incident response (DFIR) expert, you’re first on the scene when an incident occurs. Whether you’re dealing with a 50 GB business email compromise (BEC) or a multi-terabyte ransomware attack, your team needs to quickly and accurately locate personally identifiable information (PII), protected health information (PHI), and other types of regulated or high-risk data.
With Canopy, you can go from identifying what data was compromised to finding the PII within hours. Its speed allows you to deliver faster data breach response services to your clients, while its accurate PII detection can save them significant money on subsequent PII review.
Save Thousands of Hours per Incident
Canopy pairs unrivaled PII detection with AI-powered tools that speed up your data mining process. Our machine learning algorithms have detected tens of billions of PII elements and continue improving with every project.
In addition to faster data mining, Canopy's AI helps you hone your clients' PII review population, saving thousands of hours.
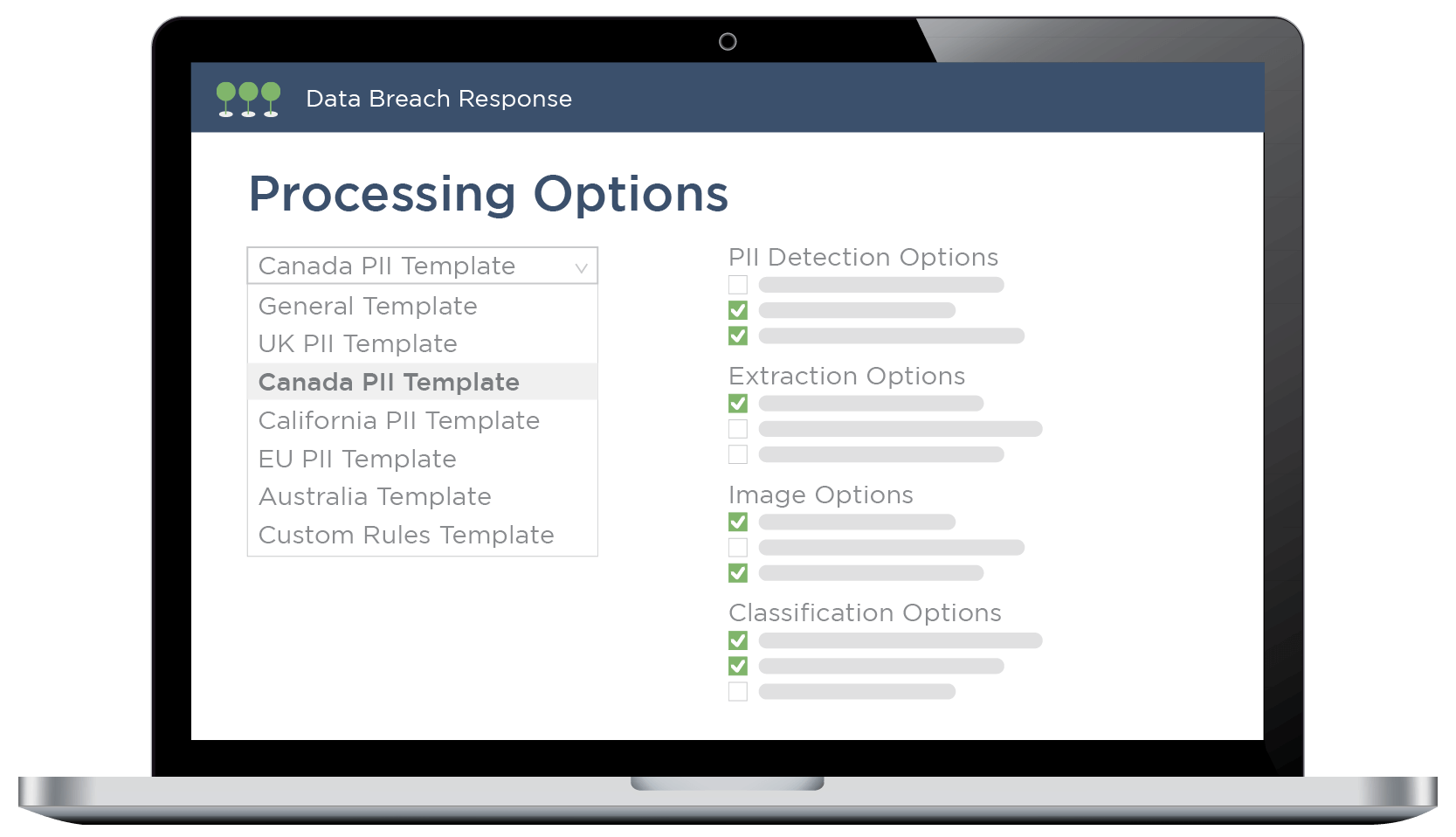
Customize Uploads with Templates
Don’t know what to look for? Our team keeps up with PII definitions across the globe.
We offer pre-built processing templates customized to different regions, regulations, and sectors. You can also save your own processing templates to serve unique needs.
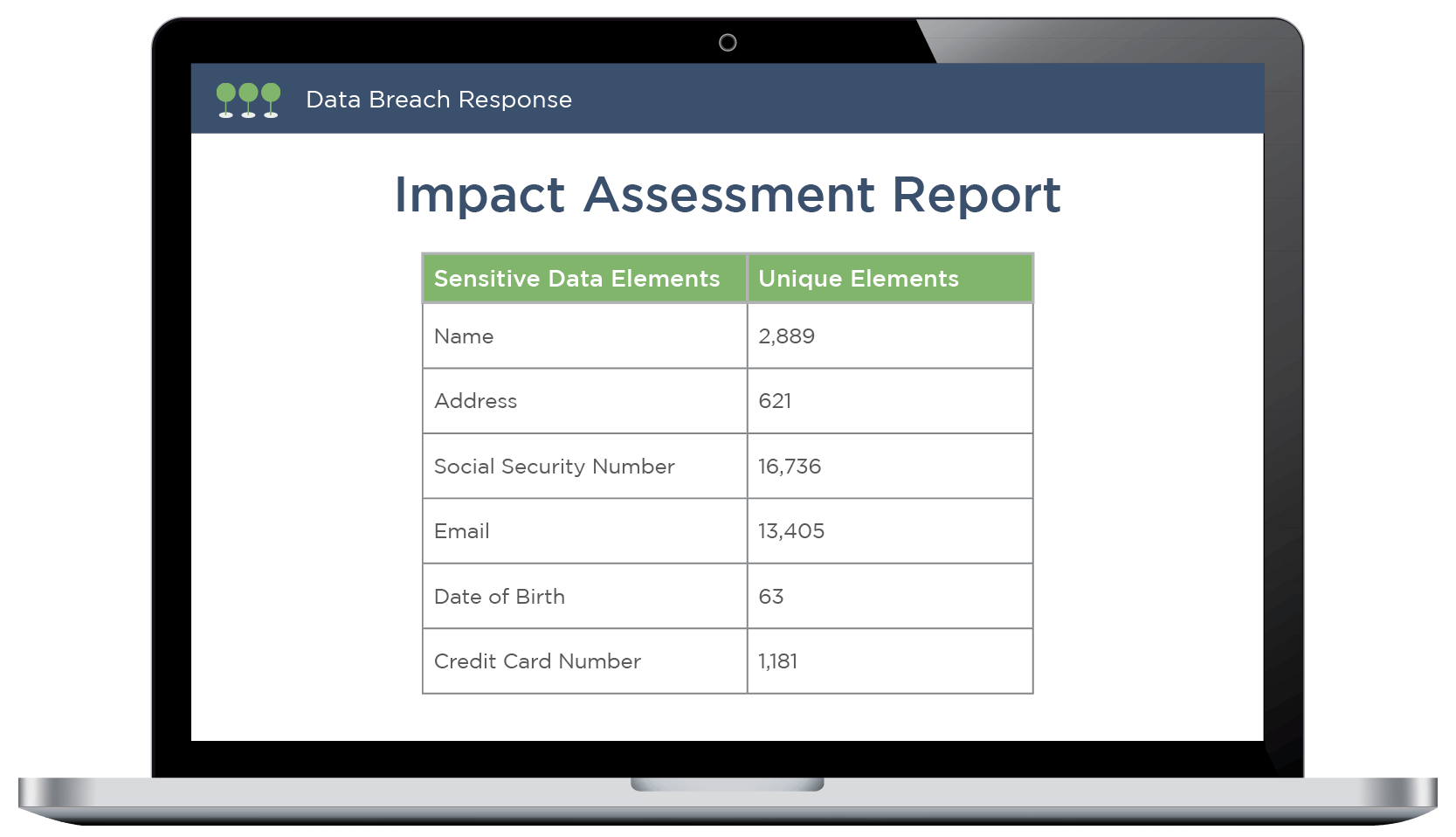
Get Clear PII Reporting
As soon as Canopy finishes processing your data (usually within hours), it generates an automatic Impact Assessment Report that provides an overview of the PII/PHI and file types detected in the data.
These insights will guide your review plan and allow legal counsel to start planning a compliant response.
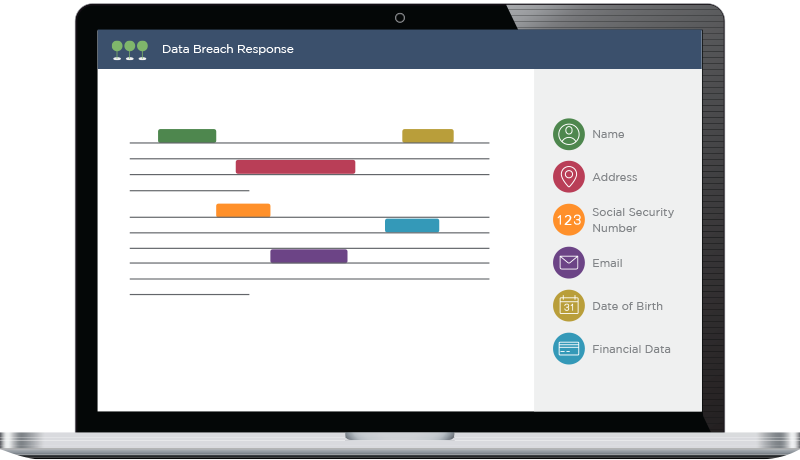
Access a Network of Review Partners
Canopy's patented AI doesn't just speed up & improve data mining — it also delivers seriously streamlined PII review. Our network of partners includes skilled review providers that are trained on the application.
When you work with a review provider that uses Canopy's Data Breach Response software, you can ensure your clients will receive fast, accurate service from start to finish.
Secure, Compliant Software
ISO 27001 Certification
We actively maintain an ISO 27001 certification and regularly conduct third-party penetration (pen) testing.
Data Security at Every Step
Data is encrypted at rest and in transit. It resides in a virtual private cloud (VPC) within your jurisdiction.
Granular Admin Control
Tenant admins can set user permissions for everything from accessing data to exporting entity lists.
Data Breach Response ≠ Ediscovery
When data breaches first became commonplace, purpose-built software for identifying PII/PHI didn't exist yet. So DFIR experts borrowed tools from forensics & ediscovery, cobbling together data mining strategies using keyword searching & regular expressions (regex).
But using ediscovery tools to data mine for PII is repetitive & time-consuming. It's also over-inclusive, resulting in huge percentages of data sets needing to be manually reviewed, which means that your clients (or their insurers) are significantly overpaying for the total cost of breach response.
By trading in ediscovery tools for Canopy's Data Breach Response software, you can complete projects much faster with less effort, and save your clients a LOT of money in the process.
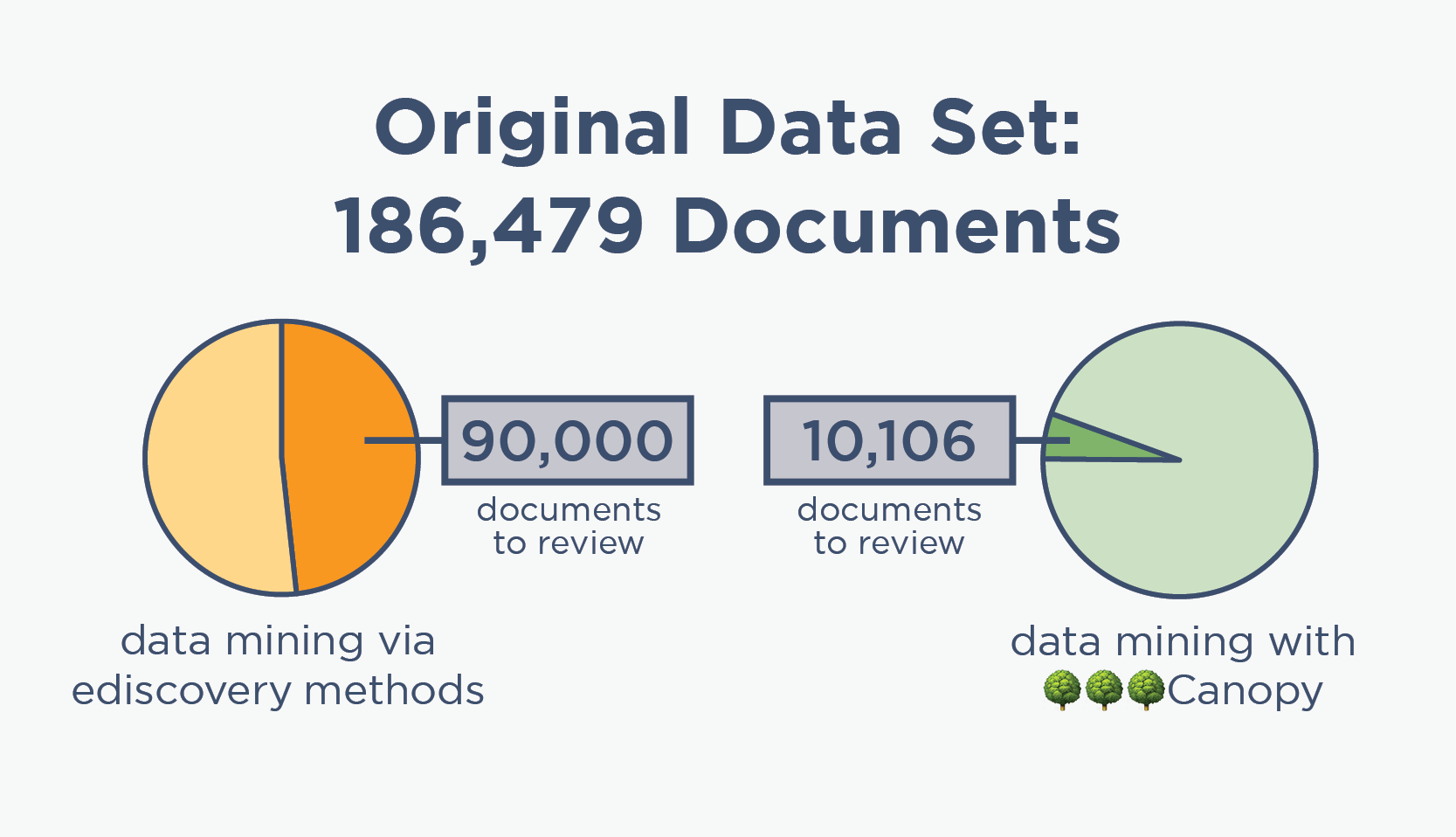
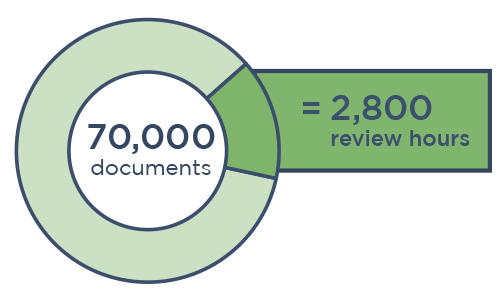
Data Mining with Canopy Saves $300,000+ in Review
“The software did a lot of the work for us upfront. If we were handling this project using traditional methods, we would have needlessly reviewed 4x as many documents to find the same amount of PII.”
ediscovery data mining
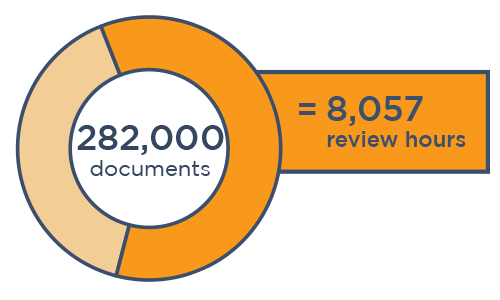
🌳🌳🌳Canopy data mining
AI + PII = The Perfect Pair
The definition of individual sensitive data classifications is consistent, making PII detection a perfect match for artificial intelligence.
Each of Canopy’s hundreds of machine learning models has a specific focus (like social security number, credit card number, religious affiliation, or diagnostic code) and is trained with thousands or even millions of examples. The application’s classifications are then validated by humans as part of the review process, helping its algorithms continuously improve.
DFIR Teams Need Purpose-Built Tools
Canopy’s Data Breach Response software leverages patented AI and machine learning technology to help DFIR teams data mine faster and more accurately, so your clients can comply with breach notification regulations and save money on their total project cost.