- Solutions
- Review & Legal Service Providers
Purpose-built for PII review.
Canopy’s AI-powered review tools help your team connect PII to people with ease, so you can deliver faster results & win more projects.
Explore Canopy's AI-Powered PII Detection
Download our brochure to learn more.
See Canopy In Action
Canopy's Data Breach Response software leverages machine learning at every step, from PII detection through to generating a notification list.
When it comes to data breach response, review & legal service providers have some unique needs. For one, you need to find the same thing every time: people and their personally identifiable information (PII), protected health information (PHI), or other types of sensitive data. You have to work within a tight deadline, too — breach notification deadlines can't be negotiated or extended like those in legal response.
Canopy's Data Breach Response software has features that speed up your PII review at every step, from administrative tools like tagging & batching documents and consolidating the entity list to a simple accept/reject workflow for reviewers that lets them work faster while limiting the risk of human error. All of this adds up to significantly reduced project costs, empowering you to bid competitively and win more data breach projects.
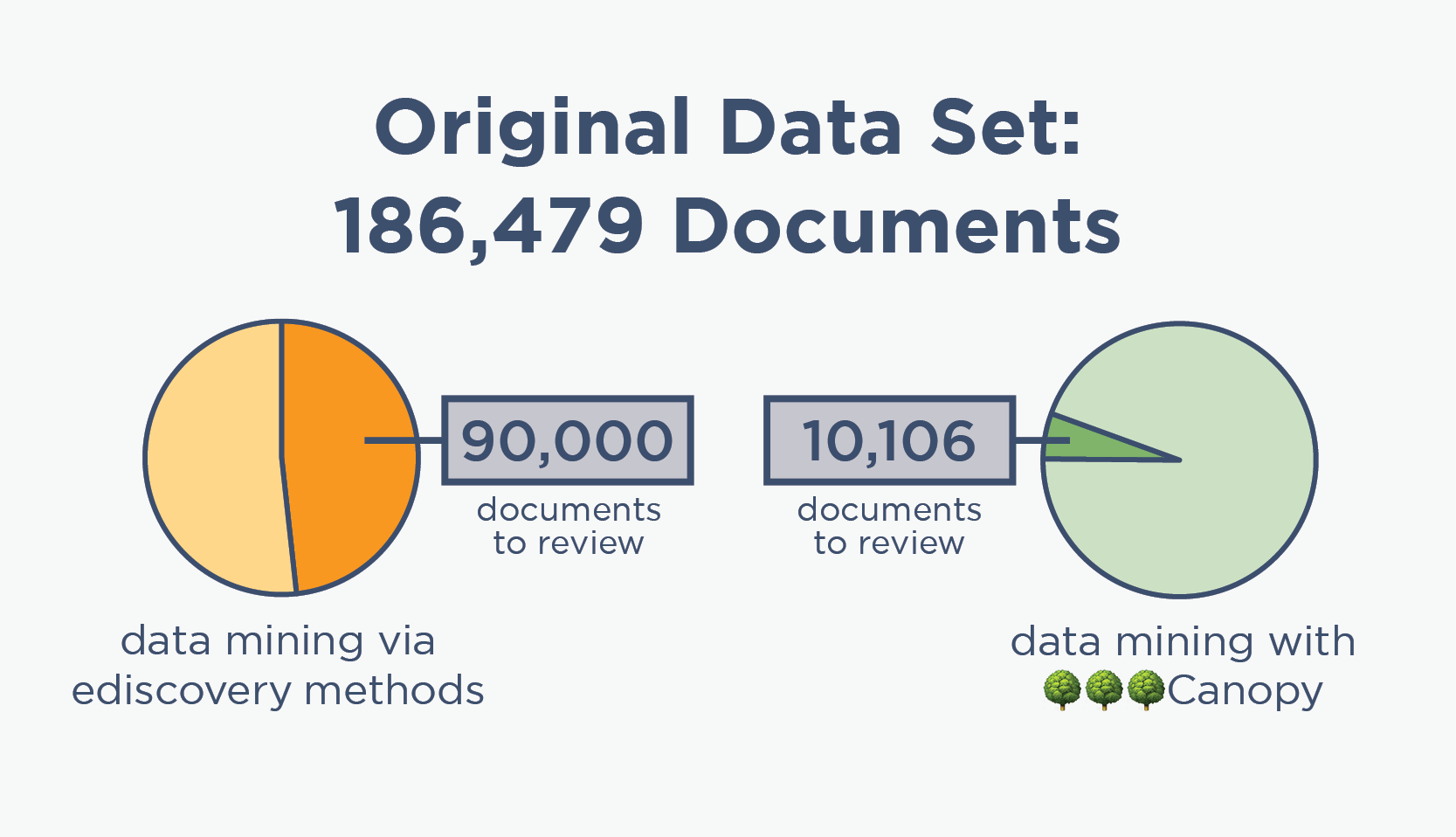
Zero In on Sensitive Documents Faster
Traditional data mining methods rely heavily on ediscovery tools, which are consistently overinclusive when it comes to PII and thus result in thousands of unnecessary documents in the review population.
Conversely, Canopy's powerful PII detection helps you focus your reviewers' efforts and deliver faster results for your clients.
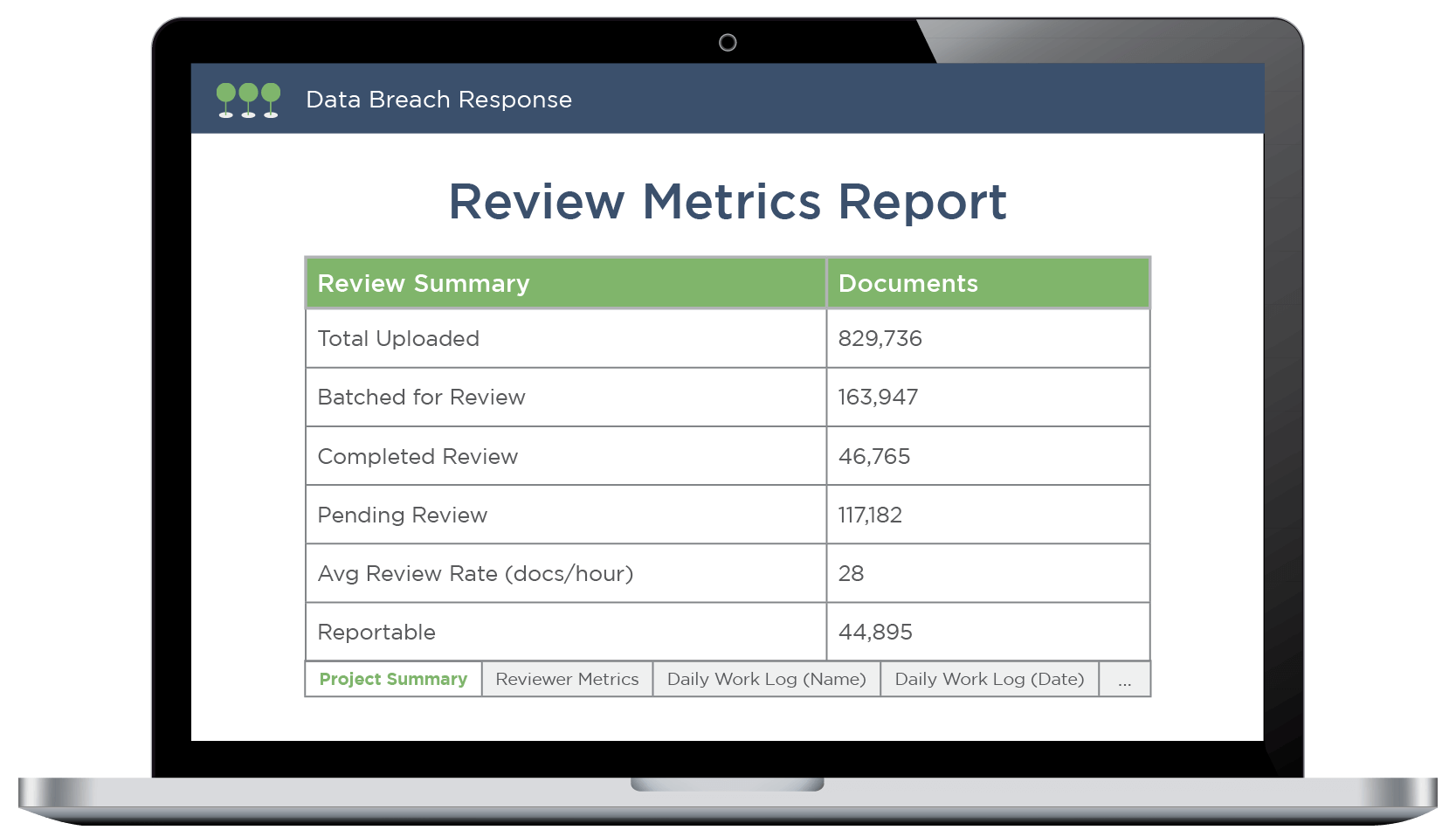
Track Progress with On-Demand Reporting
Canopy's Review Metrics Report keeps you updated on the status of your projects. Download the report for a detailed analysis at any given time, including a current project summary and breakdown of progress by day, reviewer name, and more.
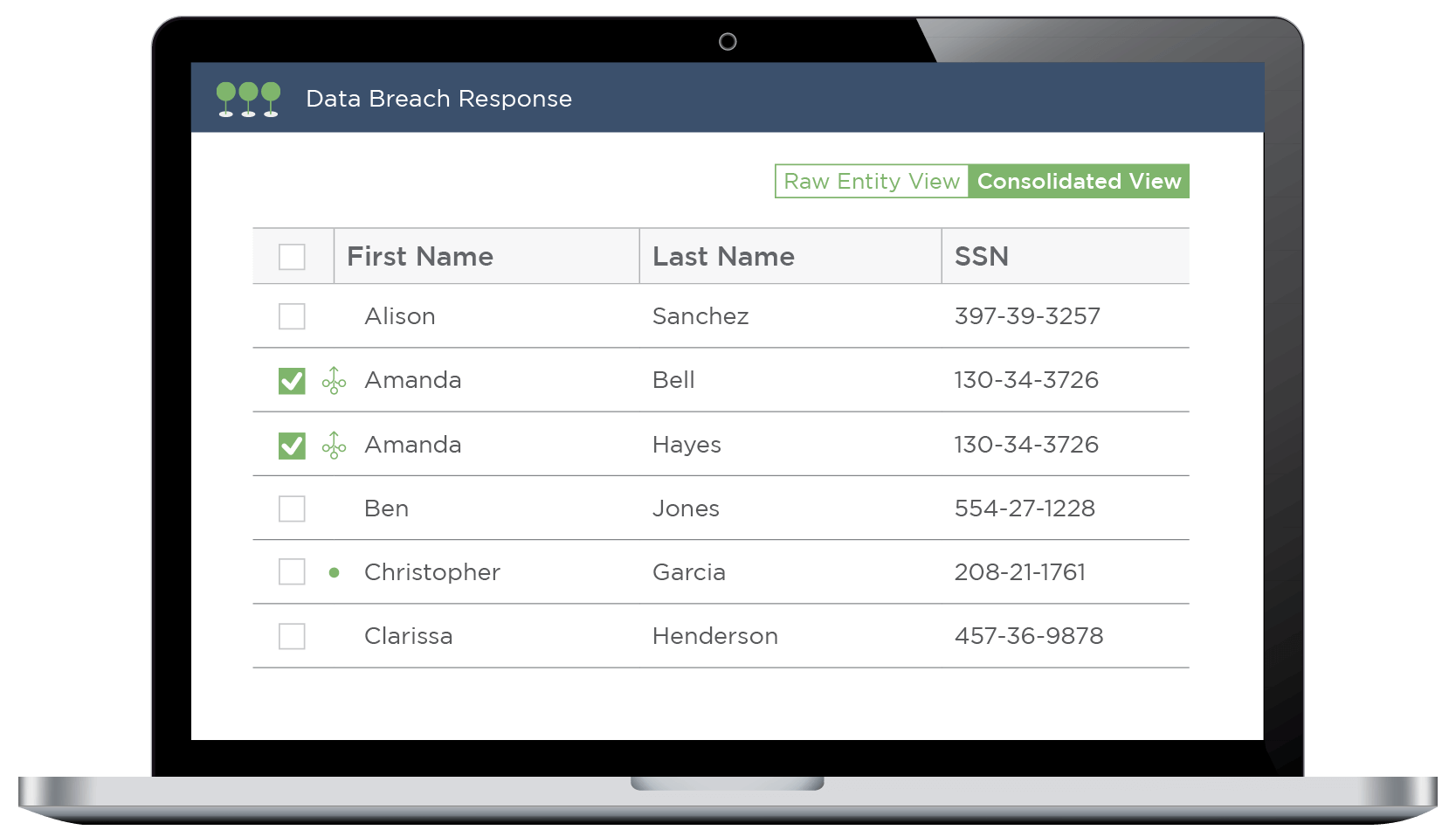
Get Your Final Entity List in Record Time
Canopy takes the pain out of consolidating your notification list. You can automatically deduplicate identical people with one click, then quickly review the application's suggestions to merge related entities, as might be seen with nicknames or maiden names.
Advanced functionality like Consolidation Rules gives you total control over this phase.
Remain Competitive in a Changing Market
Purpose-built software is here, and it's revolutionizing the entire approach to data breach response.
Review & legal service providers who have traded in their outdated ediscovery tools & techniques for Canopy are providing faster, more accurate, and less expensive services to their clients. Don't wait to be disrupted — let's team up.
Secure, Compliant Software
ISO 27001 Certification
We actively maintain an ISO 27001 certification and regularly conduct third-party penetration (pen) testing.
Data Security at Every Step
Data is encrypted at rest and in transit. It resides in a virtual private cloud (VPC) within your jurisdiction.
Granular Admin Control
Tenant admins can set user permissions for everything from accessing data to exporting entity lists.
PII Review ≠ Legal Responsiveness Review
Review providers and LSPs have traditionally handled data breach response using ediscovery tools and methodologies. That's because at a high level, these seem similar enough: they both require data processing, an initial assessment, data review, and an export. But when you look closer, the differences are apparent.
Ediscovery aims to determine which documents in a data set are legally relevant to a corporate dispute or investigation. This requires review by licensed attorneys with case-specific knowledge. On the other hand, data breach response teams must locate PII/PHI, connect that data to people, and export a notification list.
As increasingly more breached corporations seek to manage total project costs & comply with notification regulations, review and legal service providers need purpose-built data breach response tools to remain competitive & deliver faster results.
“When it comes to batching, reviewing spreadsheets, and linking compromised PII to people, other tools simply cannot compare.”
Case Study: Wotton + Kearney Speeds Up Data Breach PII Review with Canopy

76.77 GB
compromised PSTs

829,000+
documents

15
PII categories
Win More Bids with AI-Powered Review Workflows
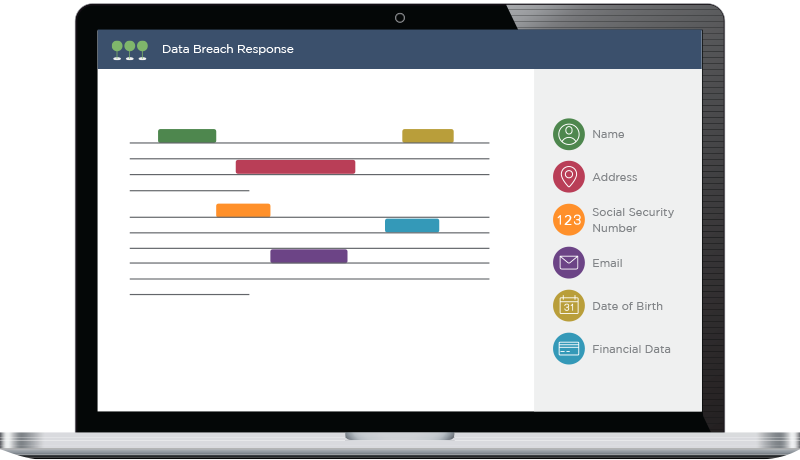
Canopy's Data Breach Response software uses AI and machine learning to help your reviewers work faster while reducing the risk of human and keystroke error. Potentially sensitive data is clearly highlighted as reviewers click through documents, enabling them to quickly connect PII to people.
As Canopy learns about a specific project, its AI turns the process of linking PII to entities into a simple “accept or reject” workflow, eliminating the need to copy-and-paste data into spreadsheets.
When you arm your reviewers with faster and more accurate tools, the total cost of data breach response is significantly lowered. That means you win more bids and your clients (and their insurance companies) benefit.
Review & Legal Service Providers Need Purpose-Built Tools
With patented AI and time-saving efficiencies, Canopy’s Data Breach Response software is made specifically for PII review. See how it can speed up your team’s workflow, providing a better service and vastly reducing your clients' incident response cost.