- Solutions
- Cyber Insurance Companies
Stop getting ripped off on cyber liability claims.
Save millions per year when your digital forensics panel providers use Canopy’s Data Breach Response software.
Explore Canopy's AI-Powered PII Detection
Download our brochure to learn more.
See Canopy In Action
Canopy's Data Breach Response software leverages machine learning at every step, from PII detection through to generating a notification list.
As businesses of all sizes process more personally identifiable information (PII) and protected health information (PHI) on their customers and employees than ever before, cyber liability insurance has evolved from an optional service to a requirement. Insurers are at an interesting crossroads: demand has never been higher, but the frequency of data breach claims and the cost of servicing them both continue to rise.
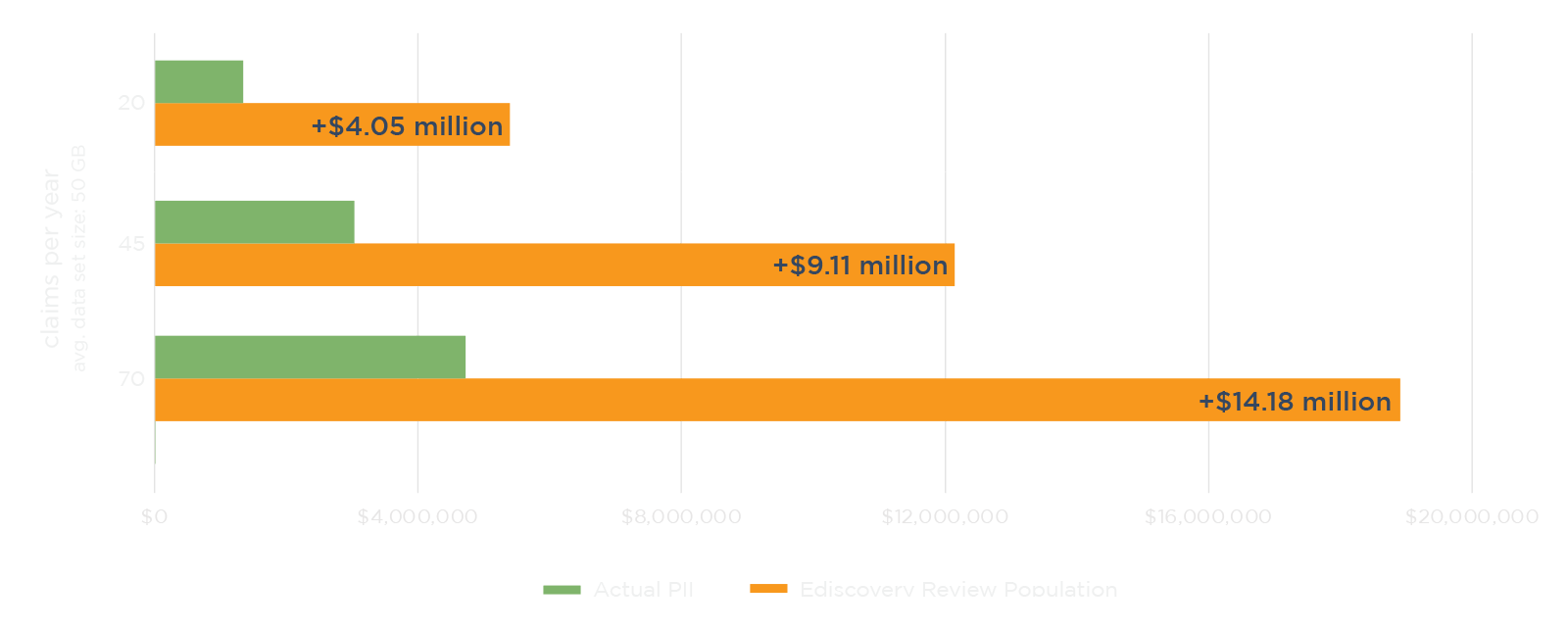
NetDiligence’s 2022 Cyber Claims Study reports that since 2017, forensics has consistently made up a significant portion — 53% on average — of the cost of crisis services for small- to medium-sized businesses (SMEs). Because insurance firms widely bear this cost, they are uniquely positioned to guide the approach to data breach response. To do that, you have to look at the total project cost — specifically, how data mining affects PII review.
Data Mining's Trickle-Down Effect
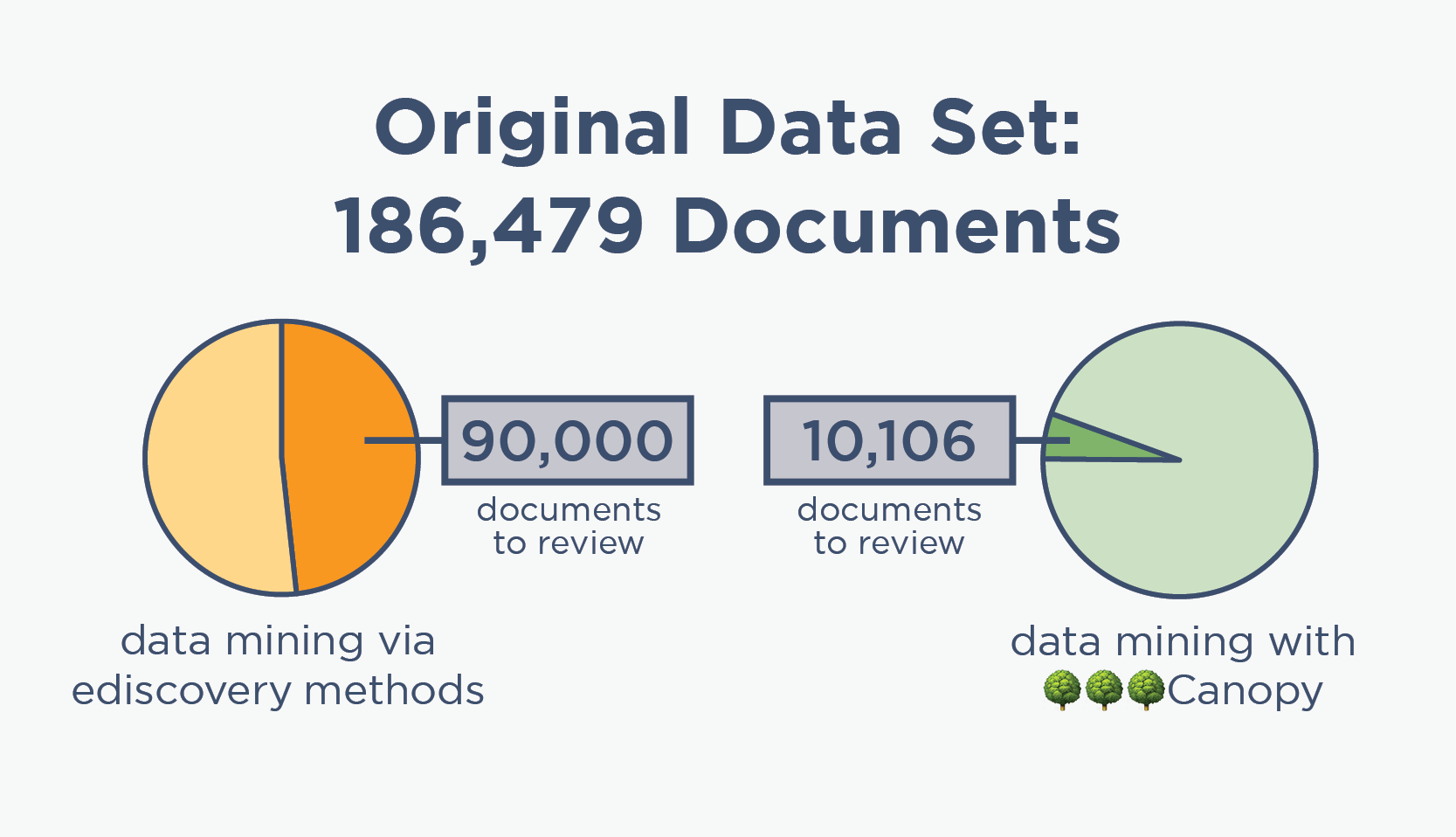
When digital forensics teams approach an incident, they start by searching for all the PII/PHI, then pass flagged documents along to human reviewers. Many data mining tools & processes are vastly over-inclusive, resulting in thousands of wasted review hours.
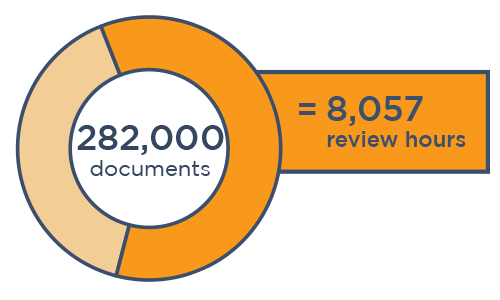
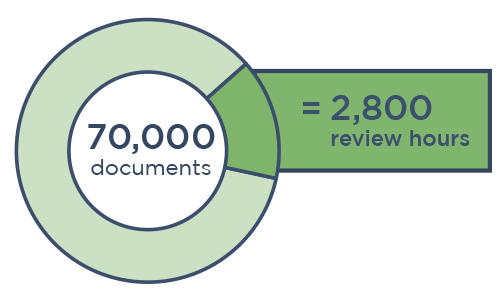
Canopy pairs unrivaled PII detection with AI-powered tools that not only speed up data mining, but also detect sensitive data with much better accuracy.
ediscovery data mining
🌳🌳🌳Canopy data mining
Better PII Detection Lowers Overall Costs
When it comes to data breach response, data mining isn't the most expensive part — the subsequent human review is. When reviewers look at thousands more documents than necessary to find PII in compromised data, the costs add up fast.
Download our case study to see how our partner saved its client (and their insurance company) over $300,000 on a relatively small project using Canopy's Data Breach Response software.
Save Millions Per Year with Canopy
“If there’s a better, faster, and cheaper alternative for data breach response, why isn’t everyone offering it?” The answer is simple: the better way is not as lucrative for many now-entrenched review providers.
Data Breach Response ≠ Ediscovery
When data breaches first became commonplace, purpose-built software for identifying PII/PHI and connecting it to the impacted people didn't exist yet. So cyber experts borrowed tools & methodologies from the closest adjacent markets: ediscovery & forensics. It was manual, repetitive, time-consuming work — but it was the best option at the time.
Using ediscovery tools to data mine for PII leads to over-inclusivity, so incident response teams need huge percentages of data sets to be manually reviewed. This means that cyber insurers pay far more than they really need to for PII review.
That all changed when Canopy launched the world’s first purpose-built software in 2018. The patented application uses machine learning to streamline the process of finding PII and connecting it to people. By trading in cobbled-together ediscovery tools for Canopy's Data Breach Response software, incident response teams can complete projects much faster at a fraction of the overall cost. But many review providers make a ton of money reviewing documents "the old way," and they don’t want this to change.
So ask your forensics & review providers how they approach data breach response. If someone today is using ediscovery tools for these projects: you’re probably getting ripped off on the review.
Secure, Compliant Software
ISO 27001 Certification
We actively maintain an ISO 27001 certification and regularly conduct third-party penetration (pen) testing.
Data Security at Every Step
Data is encrypted at rest and in transit. It resides in a virtual private cloud (VPC) within your jurisdiction.
Granular Admin Control
Tenant admins can set user permissions for everything from accessing data to exporting entity lists.
Break the Cycle of Inflated Data Mining Costs
By using panel providers that adopt the latest in AI-powered data mining and PII review software, insurers can drive down the overall cost of breach response, ultimately opening up cyber insurance to more SMEs. Explore our network of partners today.