- Solutions
- Ransomware Incidents
Data Breach Response for Ransomware Incidents
Assess the impact of ransomware incidents fast with Canopy’s Data Breach Response software.
Explore Canopy's AI-Powered PII Detection
Download our brochure to learn more.
See Canopy In Action
Canopy's Data Breach Response software leverages machine learning at every step, from PII detection through to generating a notification list.
With cyber attacks steadily on the rise, ransomware is the leading cause of loss among small to medium enterprises (SMEs). The 2023 NetDiligence® Cyber Claims Study reported that the average cost of ransomware claims by SMEs increased from $152,000 in 2018 to $865,000 in 2022, with average crisis services (including data mining) nearly tripling over that same period.
Amid these fast-rising costs, organizations that fall victim to ransomware attacks are torn in two directions. On one hand, legal counsel is pushing for regulatory compliance, which often involves meeting strict, non-negotiable deadlines. On the other, cyber insurers are increasingly more focused on managing claims costs. That means your clients need data breach response services that are cost-effective without compromising on speed and quality.
Canopy’s Data Breach Response is the only software that is purpose-built for breach response data mining. Our patented AI and machine learning streamlines the work of digital forensics & incident response (DFIR) professionals and review & legal service providers, enabling you to zero in on PII/PHI/personal data after a ransomware attack and connect that information to people faster and more accurately than any other software on the market. With Canopy, you can:
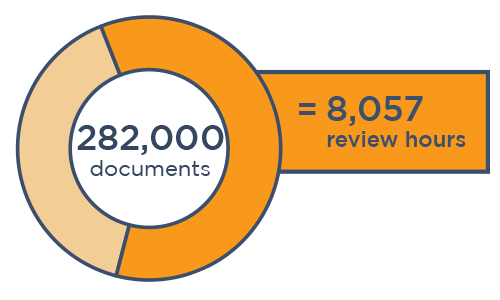
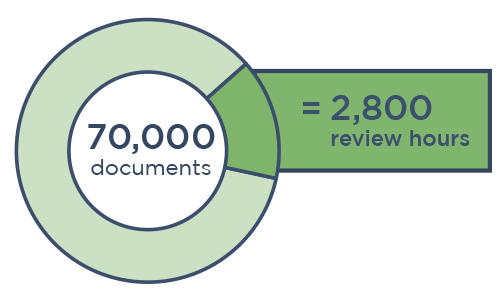
Wade Through Massive Data Sets Faster
Malicious actors target repositories likely to contain high volumes of PII, PHI, personal data, and other types of sensitive information, so ransomware incidents can easily include terabytes of data.
The Old Way
Handling data sets of this size via regex, search terms, and pattern matching can take a team of people days or even weeks just to tag documents for review.
Canopy's Solution
Canopy pairs unrivaled PII detection with AI-powered tools to exponentially speed up this process. Our machine learning algorithms have detected tens of billions of PII elements and keep improving with every project. This powerful processing means that a single person can usually estimate scope and review cost in one day, so you can deliver faster timelines and more accurate bids.
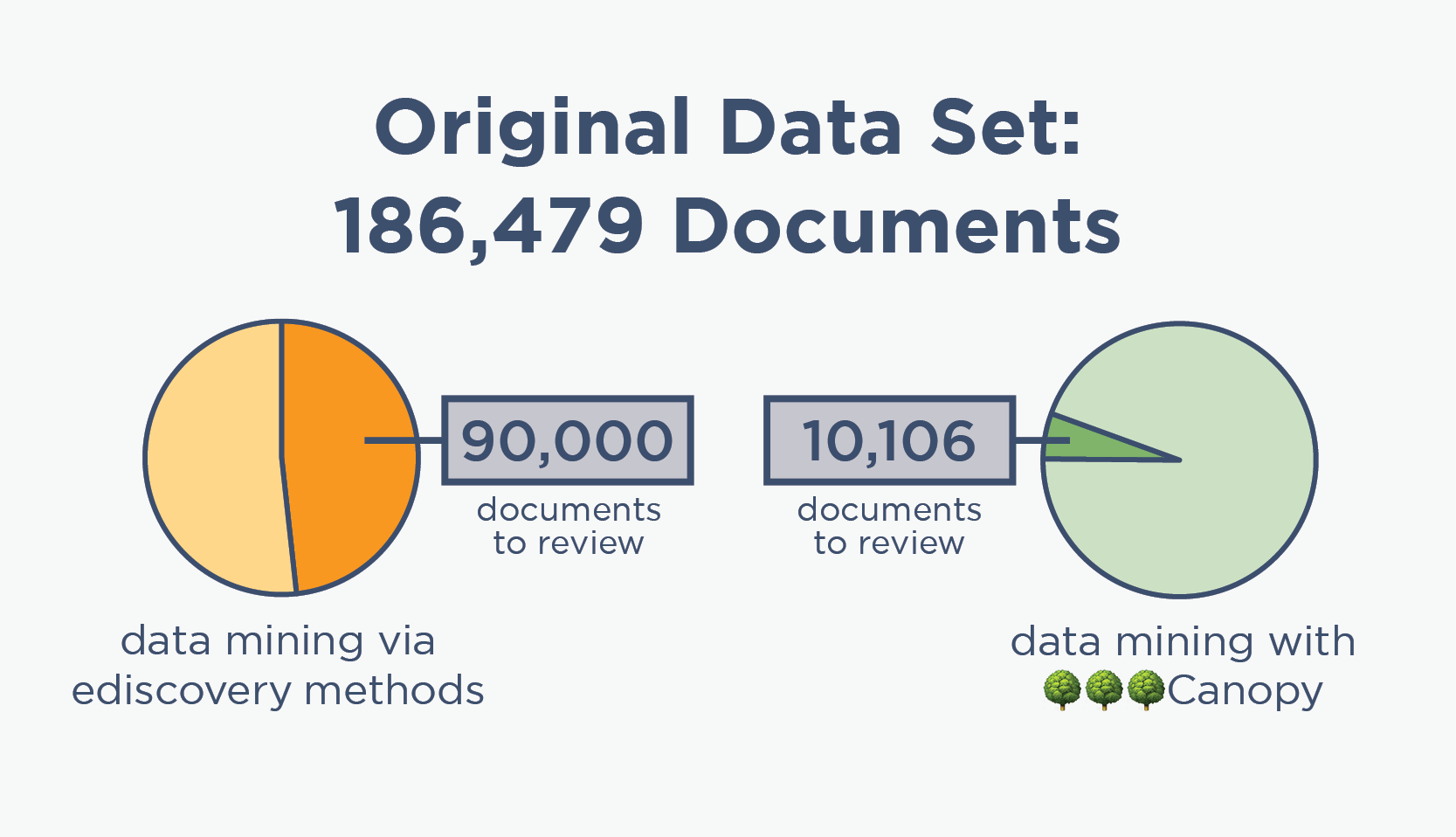
ediscovery data mining
🌳🌳🌳Canopy data mining
Streamline PII-to-People Connections
Human review is a necessary component of any breach response data mining project.
The Old Way
Many traditional document review processes involve a mix of software and spreadsheets, leaving lots of room for human and keystroke error. And the tools weren’t designed to support data breach response’s unique workflow. So it takes a lot longer than necessary, and that extra cost gets passed on to breached organizations and their cyber insurers.
Canopy's Solution
Canopy saves review teams thousands of hours per project while simultaneously decreasing this risk of error. The application clearly highlights detected PII in documents, enabling reviewers to quickly create profiles that connect people to data elements — all while maintaining links back to source documents. Our AI can even turn the process of linking PII to entities into an “accept or reject” workflow, eliminating the need to copy-and-paste data into spreadsheets.
Get Faster Insights for Legal Counsel
Not every ransomware attack results in a data breach. “Breach” is a determination that legal counsel makes after considering several factors, including what types of data were compromised, how many people were affected, and where those people live. If a breach is determined, compliance with jurisdiction- and sector-specific regulations can require strict deadlines.
When data mining with Canopy, incident response teams can provide clients’ law firms with the insights they need to make this determination much faster than with alternate tools. And if data breach notifications are required, Canopy streamlines the creation of notification lists too.
"Canopy did exactly what it was supposed to do: the software found the information we were looking for, and we got a lovely report to give to the client."
Anne Glover
Partner, Litigation & Dispute Resolution at Blakes
Watch the Webinar: The Evolution of Canada’s Data Breach Response Market
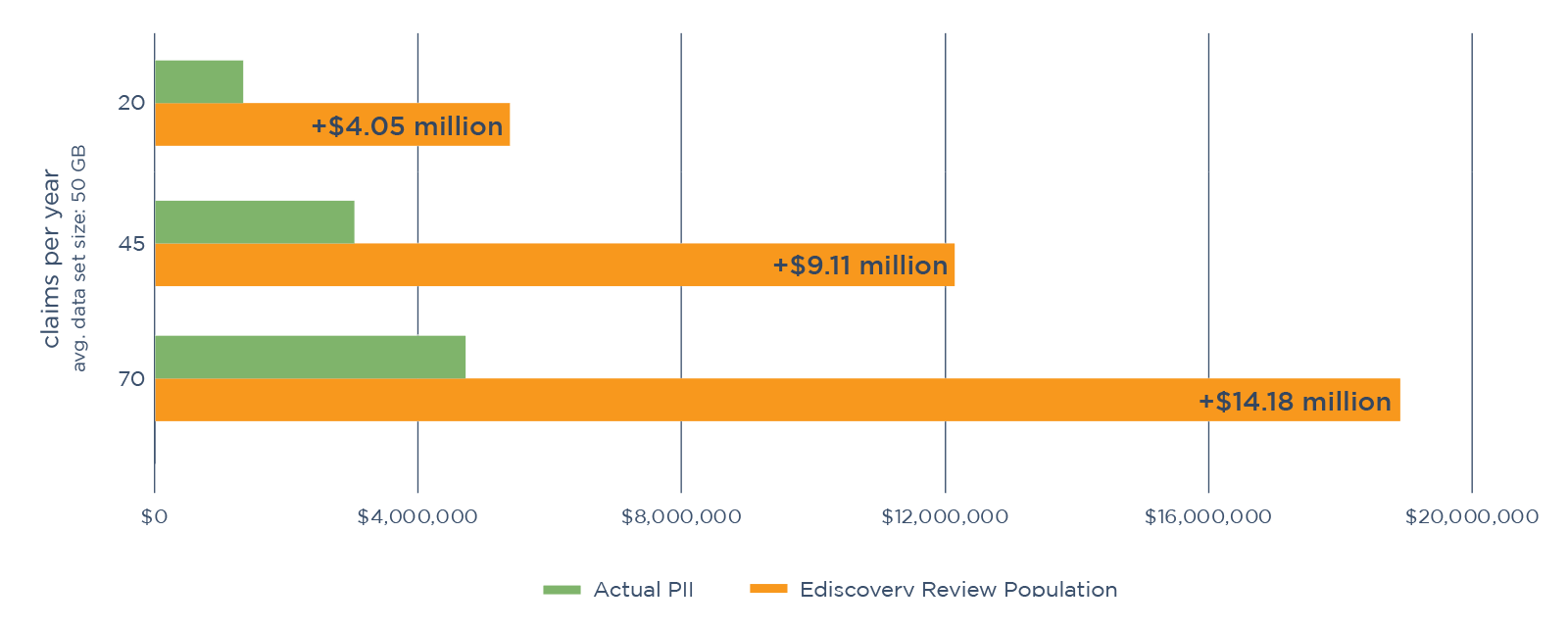
ediscovery tools & workflows can cost insurers millions of dollars more every year:
Deliver Better Results for Cyber Insurers
Cyber claims costs are going up as malicious actors improve their attack methods and become more strategic with ransom demands. Incident response teams can stand out to clients and their insurance providers by offering a more cost-effective data mining solution.
All of Canopy’s efficiencies add up to thousands or even millions of dollars saved per incident for organizations and their cyber insurers.
Save Big on Review Costs
Approach has a huge impact on data breach budgets. A single project can cost hundreds of thousands — or even millions — of dollars more when using ediscovery tools & techniques versus software that's purpose-built for data breach response.
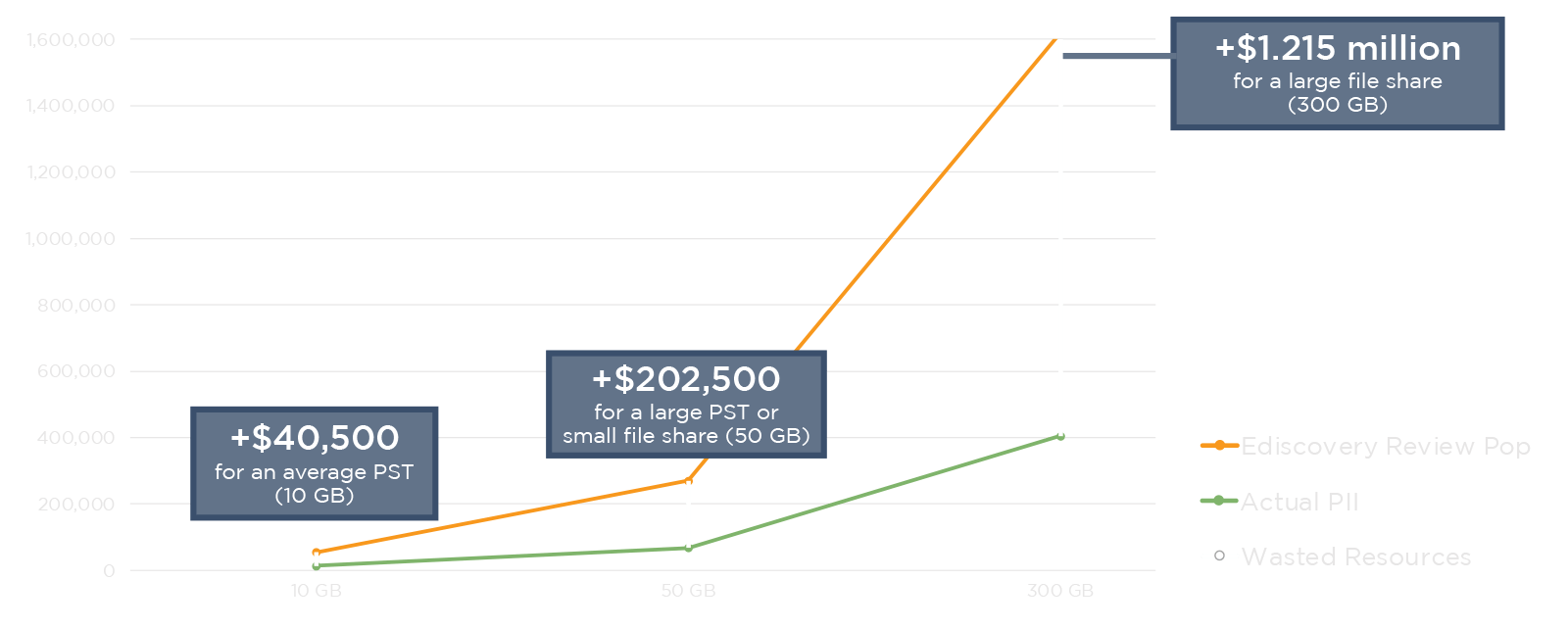
Canopy Supports an Array of File Types
Canopy works for much more than just PSTs and standard loose corporate documents. Our machine learning models analyze and categorize many types of files, including:
Databases
Canopy is the first data mining tool to support PII detection in SQL & Access databases.
Images
Canopy’s powerful AI classifies JPGs, PNGs, and other image files independently of the text on them.
Spreadsheets
Canopy takes the pain out of handling Excel and similar files, leveraging them for massive time savings downstream.
Secure, Compliant Software
ISO 27001 Certification
We actively maintain an ISO 27001 certification and regularly conduct third-party penetration (pen) testing.
Data Security at Every Step
Data is encrypted at rest and in transit. It resides in a virtual private cloud (VPC) within your jurisdiction.
Granular Admin Control
Tenant admins can set user permissions for everything from accessing data to exporting entity lists.
Software that’s Purpose-Built for Ransomware Incident Response
Leverage the patented AI and machine learning technology of Canopy’s world leading software to accurately detect personal data, make faster PII-to-people connections, and deliver better services to your data breach response clients.